- Install it with
sudo apt install shutter - Make shutter start on login within shutter go to Edit > Preferences >Behavior and choose "Start Shutter at login" on the top
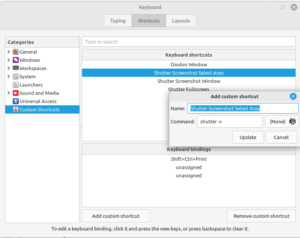
- Create custom shortcuts, open the Keyboard preferences via start menu and add three custom shortcuts:
- Shutter Screenshot Select Area:
shutter -s, shift-ctrl-print - Shutter Screenshot Window:
shutter -w, ctrl-print - Shutter Fullscreen:
shutter -f, prin
- Shutter Screenshot Select Area:
Edit 2023-12-07
Shutter has some problems lately when connected to thunderbolt dock. It leads to a black screen. I suspect 4k on my laptop together with x11.
Changed to an alternatvie, flaemshot.
To use it with printscreen follow https://flameshot.org/docs/guide/key-bindings/#on-ubuntu-and-other-gnome-based-distros and use flameshot gui as command.
Check out /usr/bin/flameshot --help.
If it flickers when taking the screenshot, it could be because of fractional scaling. Happened on a USB3 dock, probably related to https://github.com/flameshot-org/flameshot/issues/564.
Solved it with changing to 175% instead of 150%.